Telecom security is rarely simple. Most operators already juggle SS7 filtering, Diameter routing, GTP firewalls, 5G SBA migrations, roaming agreements, legacy interconnect paths and the occasional “unexpected” signalling behavior from partners. What teams often lack is a quick way to visualize their network exposure before diving into full audits or multi‑week workshops.
This is where TelcoASM comes in.
TelcoASM is a lightweight mobile network exposure assessment tool that provides a structured matrix of your security posture across major telecom domains. It is available at https://telcoasm.p1sec.com.
The idea behind TelcoASM is straightforward. Give teams a fast way to map their exposure across signalling, roaming, core network and service layers without having to assemble a 60‑page questionnaire. Engineers spend less time clicking through forms and more time discussing what actually matters: where the risks are and how to prioritize them.
Try it at https://telcoasm.p1sec.com.
What TelcoASM Measures
Telecom networks contain several control planes and interfaces that behave nothing like traditional IT systems. TelcoASM looks at the categories that consistently show up in incident reports and operator audits, such as:
• SS7 exposure including MAP and CAP
• Diameter routing posture for LTE
• GTP and mobile data control paths
• IPX and roaming connectivity
• 5G Core and SBA configuration practices
• Voice and messaging security considerations
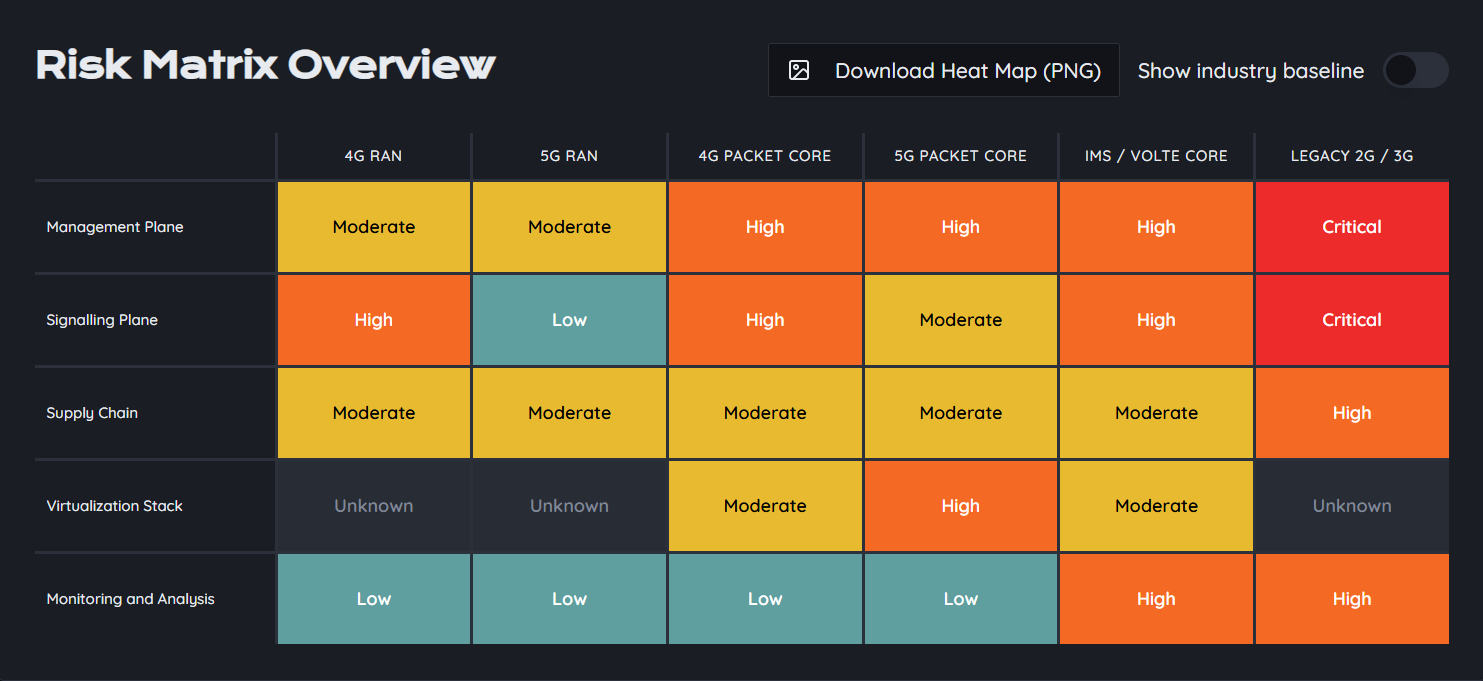
The tool provides a simple matrix view where you can assign the exposure level for each area. Nothing overly academic. Just a clear picture that helps kickstart internal discussions.
You can explore the matrix here: https://telcoasm.p1sec.com
Why Operators Use Tools Like This
Telecom threats evolve, but the root problems repeat. Misrouting policies. Over‑permissive interconnects. Weak validation on control messages. Optional features turned into production dependencies. The usual suspects.
TelcoASM is not meant to replace full audits or penetration tests. Those still matter. What it does provide is a way to:
• Establish a baseline before a deeper engagement
• Track improvements over time
• Share a common language between engineers and management
• Highlight areas that deserve a second look
• Support budget or roadmap discussions with something visual
Nothing beats a clear matrix on a slide when someone asks where the network stands.
How TelcoASM Works
- Go to telcoasm.p1sec.com
- Select exposure levels for different telecom domains
- Get an immediate posture overview that is easy to share internally
- Optionally request a deeper interpretation from P1 Security’s analysts
The tool keeps things minimal on purpose. Complex assessments rarely start well when the first step is a giant form.
For Those Heading to MWC
If you plan to attend Mobile World Congress, you can fill out your TelcoASM matrix in advance and bring it along. The P1 Security team will be able to walk through your results and discuss industry benchmarks, typical findings and areas worth prioritizing.
Start here: https://telcoasm.p1sec.com
Closing Thoughts
Telecom security benefits from clarity and shared understanding. TelcoASM provides a simple way to visualize risk across the layers that make mobile networks work. No marketing fluff. No magic scoring engine. Just a structured matrix designed by people who spend their time finding weaknesses in signalling and core networks.
Explore the tool at https://telcoasm.p1sec.com and see how your exposure map looks.
🔐 Looking for the full picture? Explore the Ultimate Guide to Mobile Network Security — your complete resource on telecom security, from architecture to audits.


.jpg)
